The vulnerability, which was reported by a man calling himself ‘Khalil,’ allows any Facebook user to post anything on the walls of other users - even when those users are not included in their list of friends. He reported the vulnerability through Facebook’s security feedback page, which offered a minimum reward of US$500 for each real security bug report.
However, the social network’s security team failed to acknowledge the bug, even though Khalil enclosed a link to a post he made on the timeline of a random girl who studied at the same college as Facebook CEO Mark Zuckerberg.
“Sorry, this is not a bug,” Facebook’s security team said in response to Khalil’s second report, in which he offered to reproduce the discussed vulnerability on a test account of Facebook security expert.

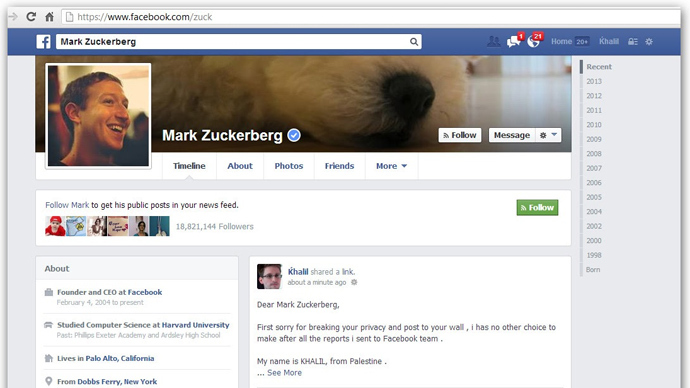
Screenshots on his blog show that Khalil shared details of the exploit, as well as his disappointing experience with the security team, on the Facebook founder’s wall.

After receiving the third bug report, a Facebook security engineer finally admitted the vulnerability but said that Khalil won’t be paid for reporting it because his actions violated the website’s security terms of service.
Although Facebook’s White Hat security feedback program sets no reward cap for the most “severe” and “creative” bugs, it sets a number of rules that security analysts should follow in order to be eligible for a cash reward. Facebook did not specify which of the rules Khalil had broken.
Somewhere between the second and third vulnerability reports, Khalil also recorded a video of himself reproducing the bug.
In its latest reply, Facebook reinstated Khalil’s account and expressed hope that he will continue to work with Facebook to find more vulnerabilities.
see result here: http://on.rt.com/2ylp9k
Khalil reported a bug so is entitled to the reward. The fact that Facebook's security team failed to detect it as authentic makes them accountable for Khalil having to take an alternative route to prove himself. I'm of the opinion that the reward money should be taken directly out of the engineer/s pocket/s.
ReplyDeleteCoooooooooL :-) خليل الملك هعععع
ReplyDelete